Table of Contents
What Is BEC?
Business email compromise (BEC) is a type of email information-seeking scam in which an attacker targets a business to defraud the company. Business email compromise is a large and growing problem that targets organizations of all sizes across every industry around the world. BEC scams have exposed organizations to billions of dollars in potential losses.
Email account compromise (EAC), or email account takeover, is a related threat that is accelerating in an era of cloud-based infrastructure. EAC is often associated with BEC because compromised accounts are used in a growing number of BEC-like scams (though EAC is also the basis of other kinds of cyber attacks).
BEC and EAC are difficult to detect and prevent, especially with legacy tools, point products and native cloud platform defenses.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we'll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
Types of Business Email Compromise
The FBI defines 5 major types of BEC scams:
- CEO Fraud: Here the attackers position themselves as the CEO or executive of a company and typically email an individual within the finance department, requesting funds to be transferred to an account controlled by the attacker.
- Account Compromise: An employee’s email account is hacked and is used to request payments to vendors. Payments are then sent to fraudulent bank accounts owned by the attacker.
- False Invoice Scheme: Attackers commonly target foreign suppliers through this tactic. The scammer acts as if they are the supplier and request fund transfers to fraudulent accounts.
- Attorney Impersonation: This is when an attacker impersonates a lawyer or legal representative. Lower level employees are commonly targeted through these types of attacks where one wouldn’t have the knowledge to question the validity of the request.
- Data Theft: These types of attacks typically target HR employees in an attempt to obtain personal or sensitive information about individuals within the company such as CEOs and executives. This data can then be leveraged for future attacks such as CEO Fraud.
How Do BEC Attacks Work?
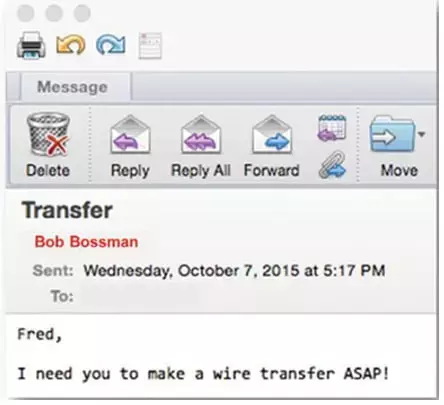
In a BEC scam, the attacker poses as someone the recipient should trust—typically a colleague, boss or vendor. The sender asks the recipient to make a wire transfer, divert payroll, change banking details for future payments and so on.
BEC attacks are difficult to detect because they don’t use malware or malicious URLs that can be analyzed with standard cyber defenses. Instead, BEC attacks rely instead on impersonation and other social engineering techniques to trick people interacting on the attacker’s behalf.
Because of their targeted nature and use of social engineering, manually investigating and remediating these attacks is difficult and time consuming.
BEC scams use a variety of impersonation techniques, such as domain spoofing and lookalike domains. These attacks are effective because domain misuse is a complex problem. Stopping domain spoofing is hard enough—anticipating every potential lookalike domain is even harder. And that difficulty only multiplies with every domain of an outside partner that could be used in a BEC attack to exploit users’ trust.
In EAC, the attacker gains control of a legitimate email account, allowing them to launch similar BEC-style. But in these cases, the attacker isn’t just trying to pose as someone—for all practical purposes, the attacker is that person.
Because BEC and EAC focus on human frailty rather than technical vulnerabilities, they require a people-centric defense that can prevent, detect, and respond to a wide range of BEC and EAC techniques.
PHASE 1 – Email List Targeting
The attackers begin by building a targeted list of emails. Common tactics include mining LinkedIn profiles, sifting through business email databases, or even going through various websites in search of contact information.
PHASE 2 – Launch Attack
Attackers begin rolling out their BEC attacks by sending out mass emails. It’s difficult to identify malicious intent at this stage since attackers will utilize tactics such as spoofing, look-alike domains, and fake email names.
PHASE 3 – Social Engineering
At this stage attackers will impersonate individuals within a company such as CEOs or other individuals within finance departments. It’s common to see emails that request urgent responses.
PHASE 4 – Financial Gain
If attackers can successfully build trust with an individual, this is typically the phase where financial gain or data breach is made.
How Do I Protect Against BEC Exploits?
BEC and EAC are complex problems that require multi-layered defenses. Effectively stopping these exploits means:
- Stopping the wide range of BEC/EAC tactics.
- Getting visibility into malicious activities and user behavior—both within your environment and in the cloud.
- Automating detection and threat response.
An effective BEC/EAC defense secures all of the channels that attackers exploit. These include corporate email, personal webmail, business partners’ email, cloud apps, your web domain, the web and users’ own behavior.
Because BEC and EAC rely on a willing (though unwitting) victim, attack visibility, email protection and user awareness all play key roles in an effective defense.
Train your users to look for these signs that the email may not be what it seems:
- High-level executives asking for unusual information: How many CEOs actually want to review W2 and tax information for individual employees? While most of us will naturally respond promptly to an email from the C-suite, it's worth pausing to consider whether the email request makes sense. A CFO might ask for aggregated compensation data or a special report, but individual employee data is less likely.
- Requests to not communicate with others: Impostor emails often ask the recipient to keep the request confidential or only communicate with the sender via email.
- Requests that bypass normal channels: Most organizations have accounting systems through which bills and payments must be processed, no matter how urgent the request. When these channels are bypassed by an email directly from an executive requesting, for example, that an urgent wire transfer be completed ASAP, the recipient should be suspicious.
- Language issues and unusual date formats: Some lure emails have flawless grammar, and some CEOs write emails in broken English. But the presence of European date formats (day month year) or sentence construction that suggests an email was written by a non-native speaker are common in many of these attacks.
- Email domains and “Reply To” addresses that do not match sender’s addresses: Business Email Compromise emails often user spoofed and lookalike sender addresses that are easy to miss if the recipient isn’t paying attention. (yourc0mpany.com instead of yourcompany.com, for example).
Robust email security, domain authentication, account protection, content inspection and user awareness must work together in a holistic fashion.
Protect Against BEC Attacks
Here are a few tips to protect against BEC and EAC scams and keep organizations safe in the face of these increasingly common attacks:
- Be suspicious. Asking for clarification, forwarding an email to IT, or checking with a colleague is better than wiring hundreds of thousands of dollars to a fake company in China.
- If something doesn't feel right, it probably isn't. Encourage employees to trust their instincts and ask “Would my CEO actually tell me to do this?” or “Why isn't this supplier submitting an invoice through our portal?”
- Slow down. Attackers often time their campaigns around our busiest periods of the day for good reason. If a human resources manager is quickly going through emails, she is less likely to pause and consider whether a particular request is suspect.
Learn More About BEC and EAC Threats
Impostor emails are purpose-built to impersonate someone your users trust and trick them into sending money or personal information to cyber criminals. Proofpoint is the only vendor that can provide an integrated, holistic solution that addresses all attackers’ tactics, provides visibility into malicious activities and user behavior, and automates detection and threat response.