
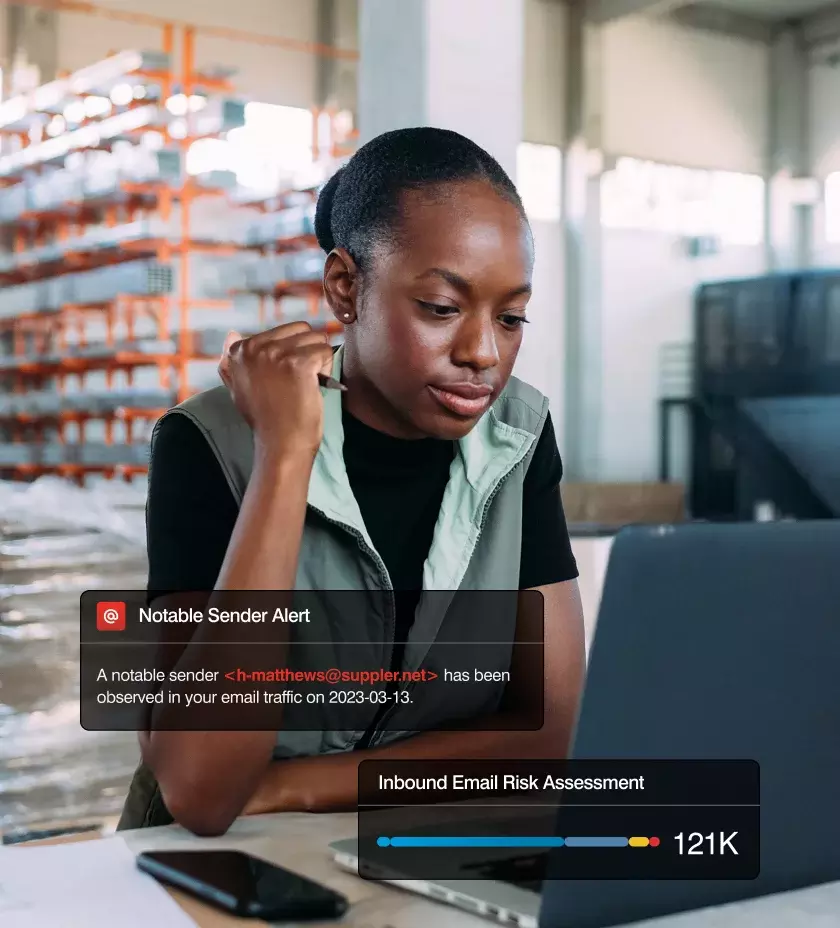
Holistic brand and supplier defense that stops 100% of spoofing
Impersonation puts your business at risk. Attacks that spoof trusted domains, executives, suppliers and applications can result in customer mistrust, brand damage, and significant financial losses.
Our holistic impersonation protection defends your business communications from brand abuse and detects compromised supplier accounts.
Simplified email authentication that protects your business from domain abuse
Supplier account defense that uses behavioral AI, machine learning and threat intelligence to protect you from compromised suppliers
Malicious lookalike domain detection reveals a complete view of newly registered domains that pose as your brand
Holistic impersonation protection, simplified
We stop 100% of domain spoofing
Our experts help you authenticate your email and guide you through each stage of a DMARC rollout so attackers can’t pose as you. And we integrate your domain protection with our Threat Protection solution, so you can ensure protection without blocking legitimate mail, reducing your team’s workload.
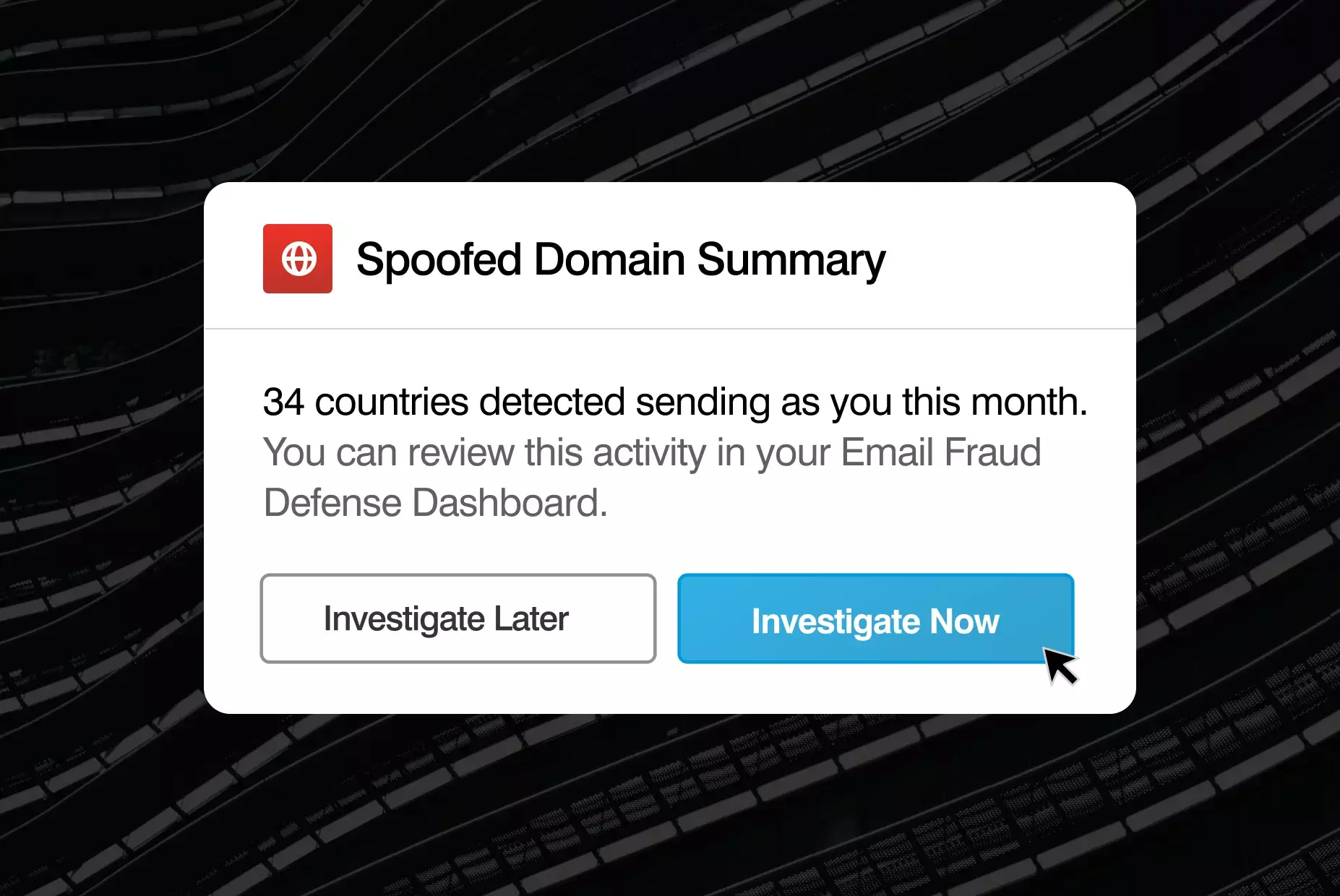
The best lookalike domain defense
We actively detect and flag registered lookalike domains posing as you. And we can remove them via the registrar or hosting provider. We also actively uncover malicious lookalikes of your suppliers’ domains, enabling you to implement adaptive controls.
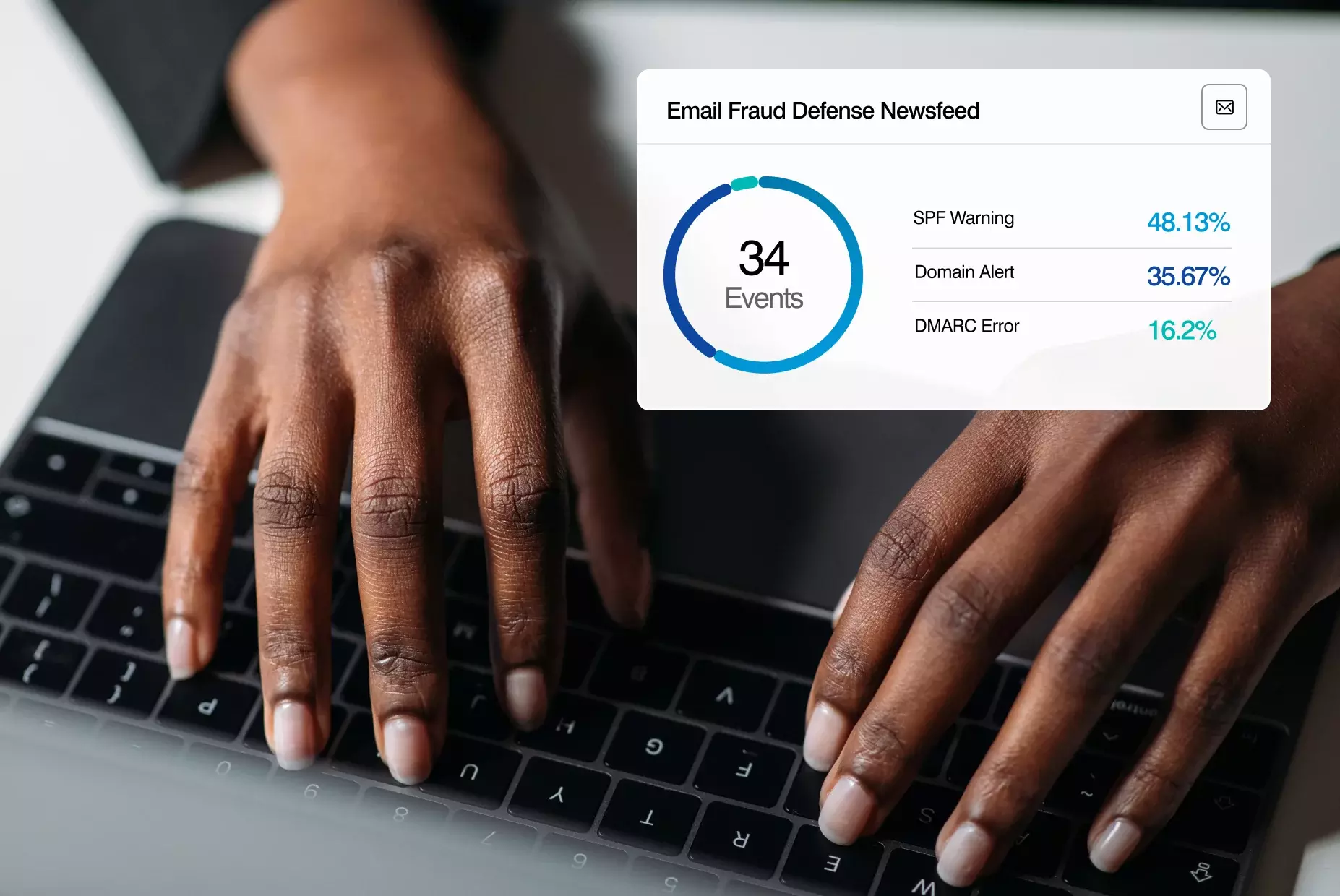
Defend against compromised suppliers
We help you detect and defend against risky suppliers using behavioral AI, machine learning and threat intelligence. Our adaptive controls mitigate your exposure and integrate with our threat protection solution to provide context around sender-recipient relationships and streamline third party incident response and investigation.
Prevent hijacked application email
Application emails sent “as you” like password resets, order confirmations, appointment reminders and service updates are critical. We ensure those emails are authenticated and secure, relieving the burden on your security team and ensuring seamless business operations.
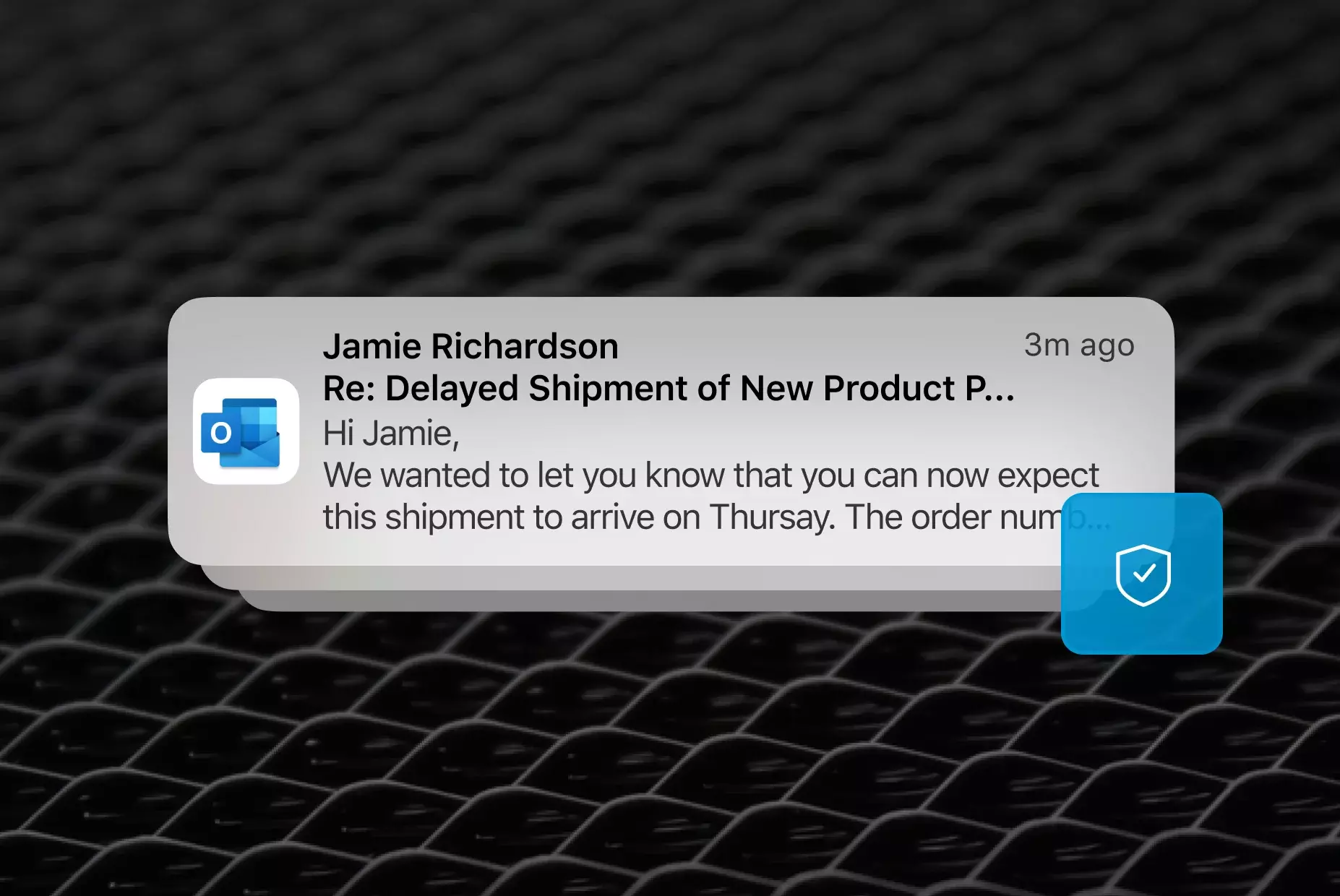
Secure Email Deliverability
Proofpoint secures email deliverability for both your outbound user email and application email. While your competitors may end up in the spam folder due to unauthenticated application email, we keep you in compliance with major email service providers like Google and Yahoo.
Comprehensive solution
Our holistic approach empowers your team with total visibility into all impersonation risks including domain spoofing, malicious lookalike domains and compromised supplier accounts. And we reveal all emails being sent as you, including 3rd parties and applications. Instead of juggling multiple vendors tackling different pieces of the impersonation problem, you can simplify with a single vendor to tackle the whole problem.
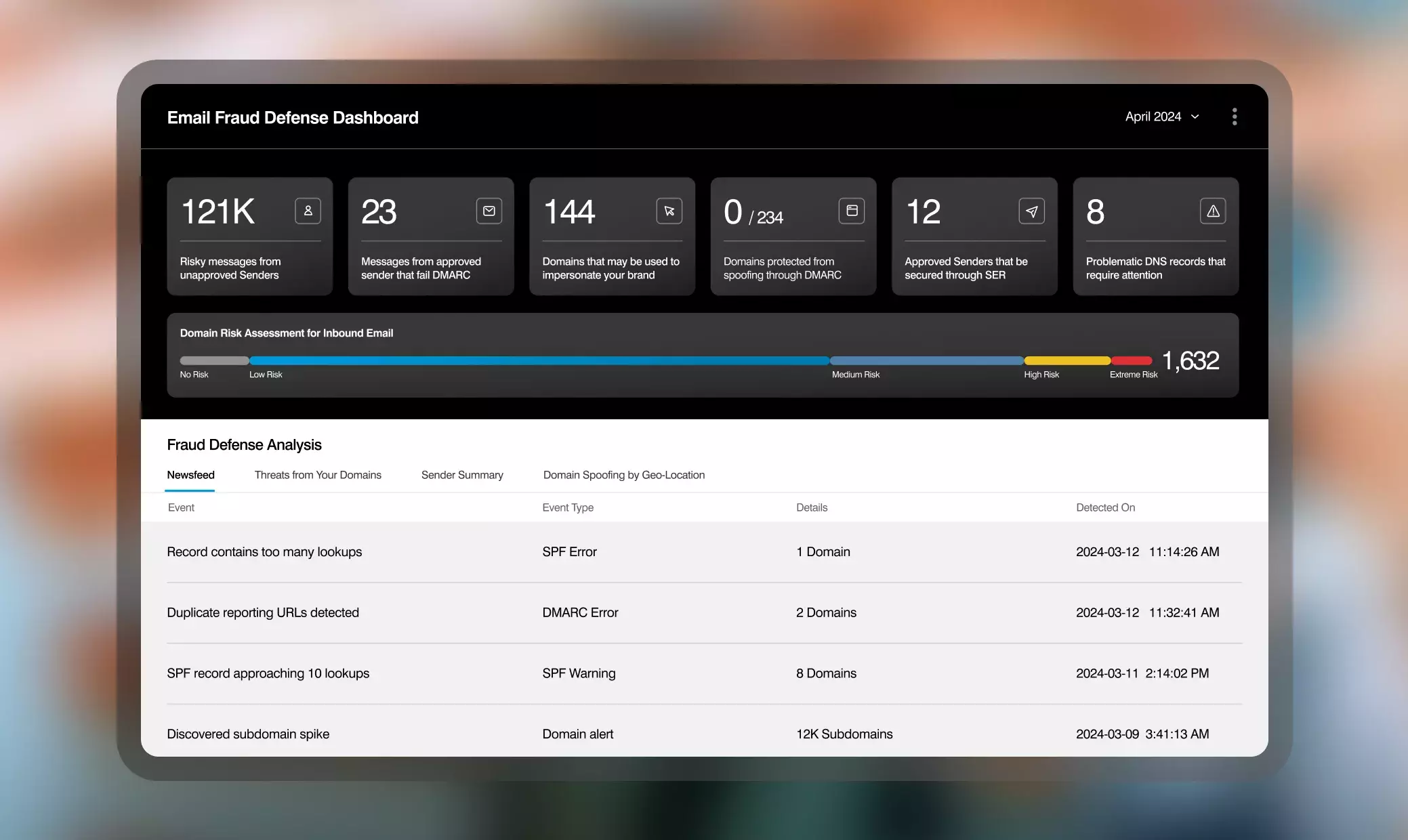
Key features of our Impersonation Protection product
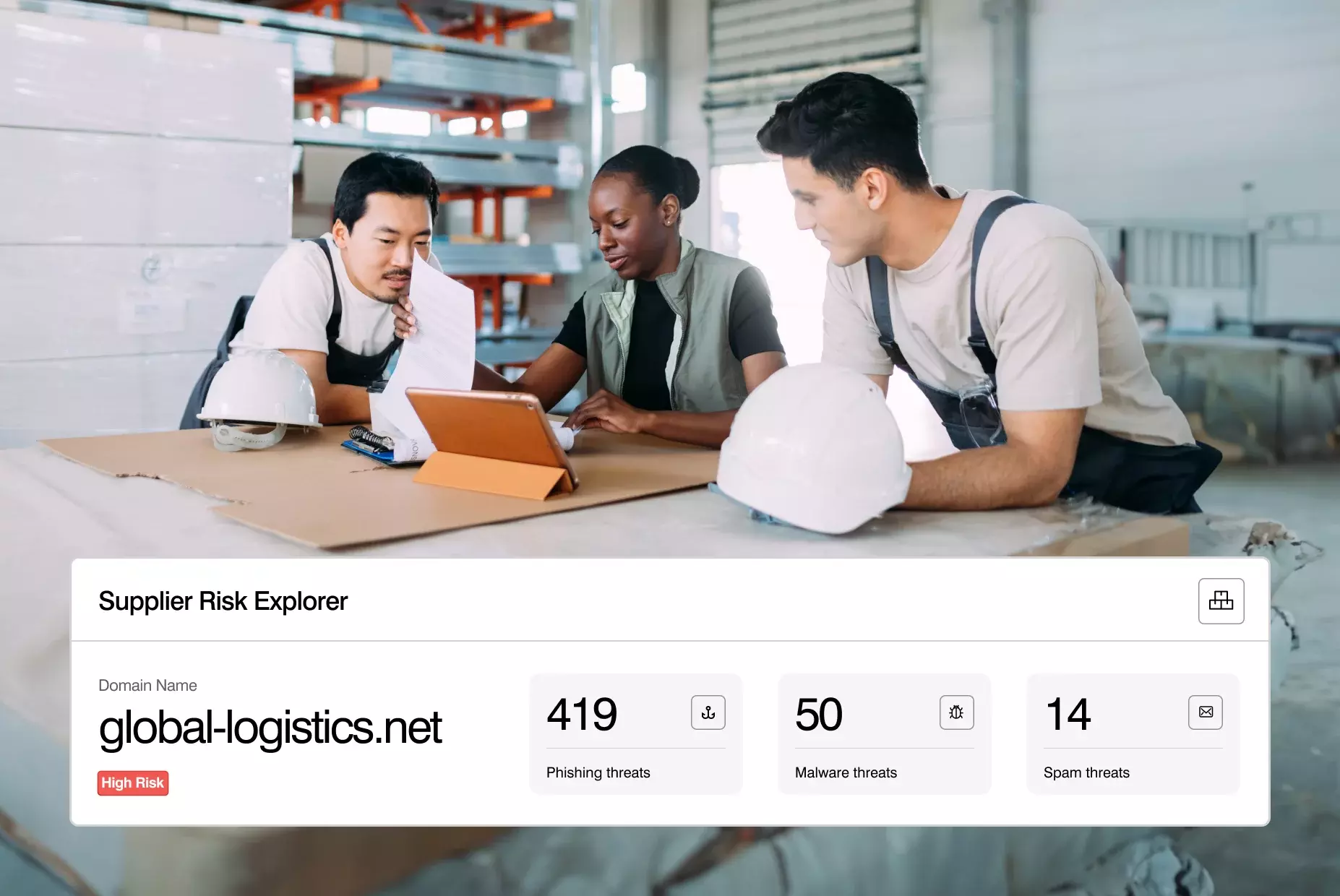
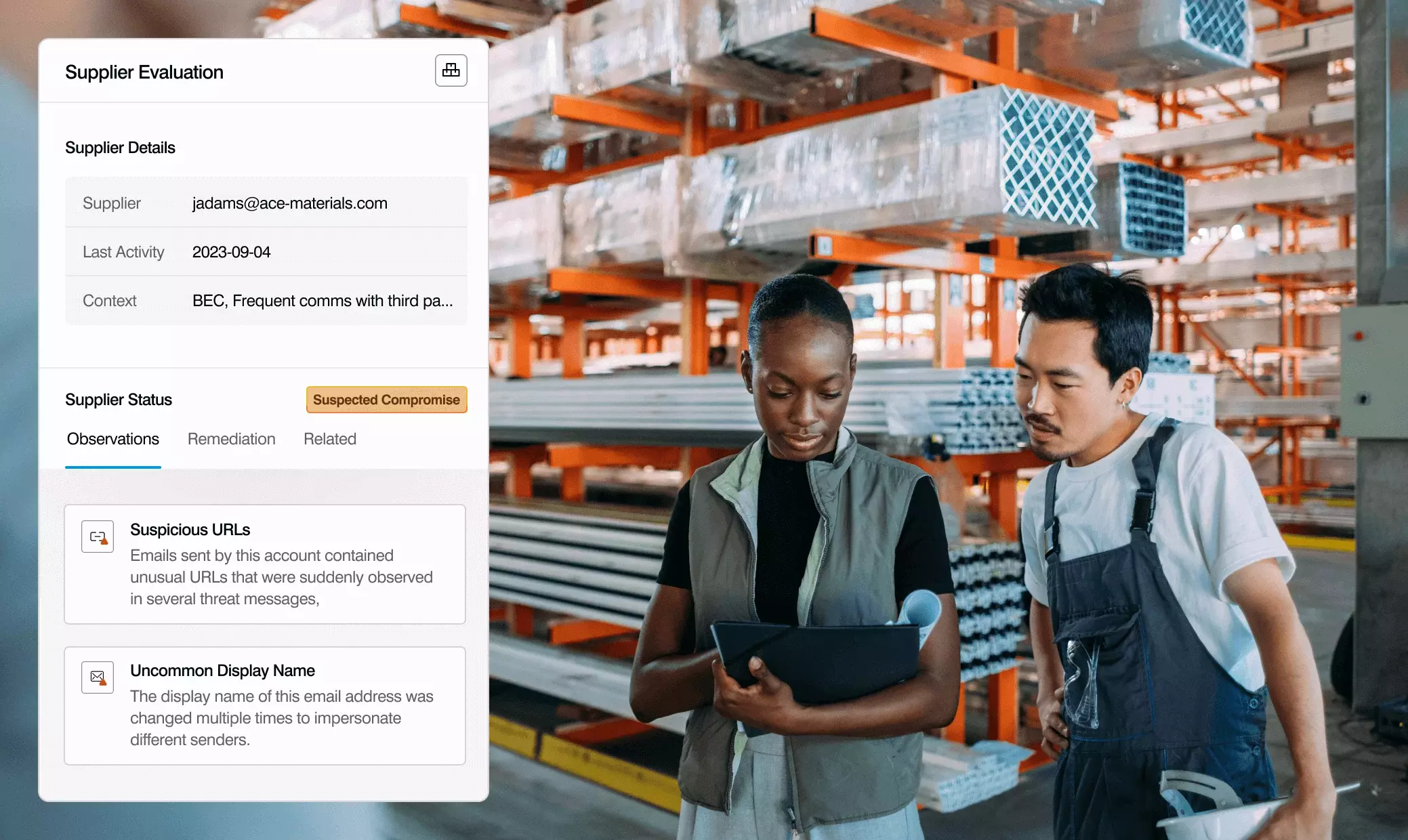
Uncover compromised supplier accounts
We correlate behavioral AI, machine learning and threat intelligence to proactively uncover compromised supplier accounts. And we integrate with our threat protection solution provide sender-recipient context to streamline your response.
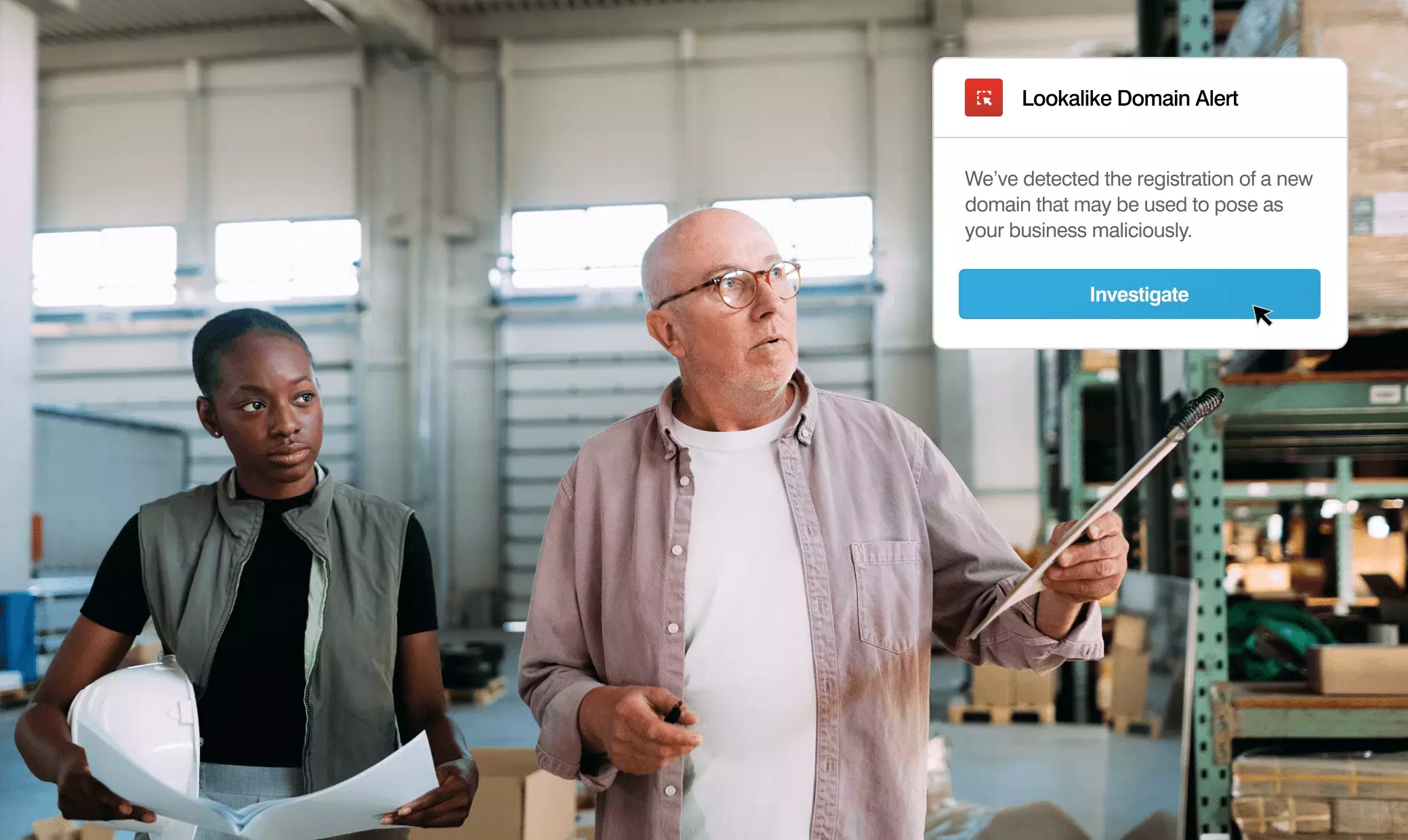
Dynamic detection of lookalike domains
We dynamically detect new registered domains that pose as your business and uncover malicious lookalike domains of your suppliers, revealing the messaging volume and messages delivered from those malicious lookalikes. No other vendor can provide that kind of visibility.
DMARC implementation, simplified
DMARC implementation can be complex. Our expert consultants will guide you through each step of your DMARC rollout. With us, you’ll get comprehensive visibility into email authentication for all of your emails —including authorized 3rd parties, user and application email.
Adaptive controls to mitigate risk
We allow customers to apply adaptive controls, such as automatic isolation of URLs from compromised supplier accounts without disrupting your business. Others cannot give you adaptive controls to mitigate risk.
Our industry-leading detection stack secures outbound email
We apply our industry-leading threat detection stack to all your application email sent as you to ensure your outbound email traffic is clean and secure.
“That kind of security — protecting our brand — is priceless.
Scott Lymer
Senior Information Security Analyst,
Shelter Insurance
The latest developments in Impersonation Protection

Getting Started with DMARC
Read More
Email Authentication Kit

Impersonation Protection Solution Brief
Turn people into your best defense
Get Started
Product Packages
Comprehensive protection against today's risks — tailored to your organization's needs.
Learn MoreGet Up to Speed
Explore the latest in cybersecurity news, insights, and innovations.
Resource LibraryTake an Assessment
Get a security audit and custom report of your corporate environment
GET AN ASSESSMENT